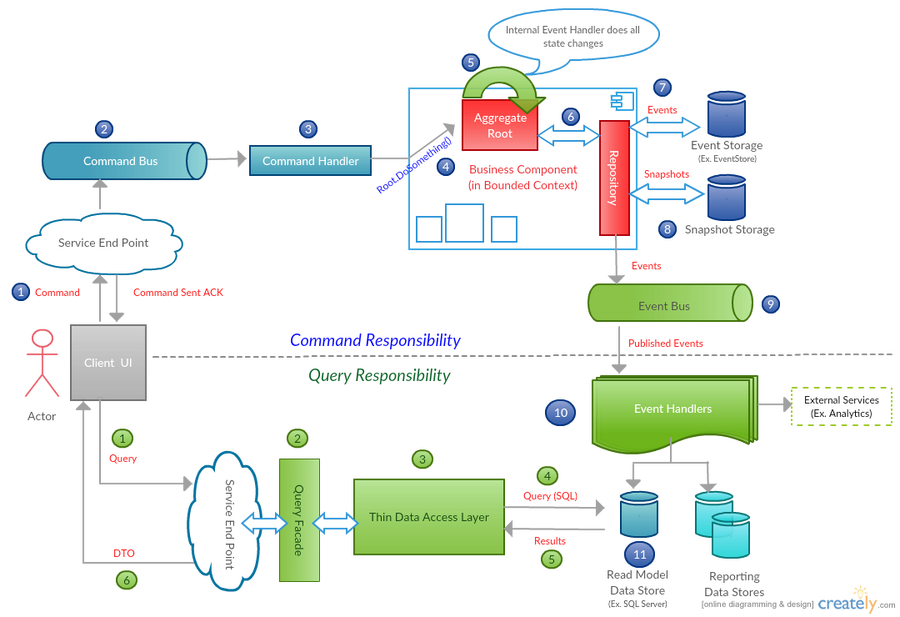
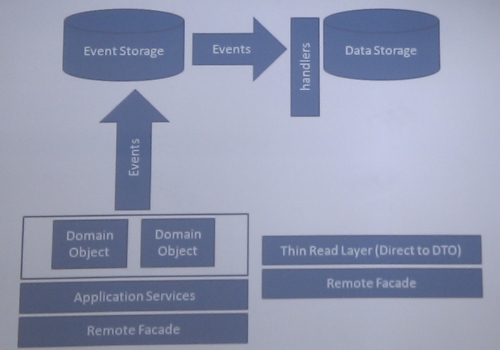
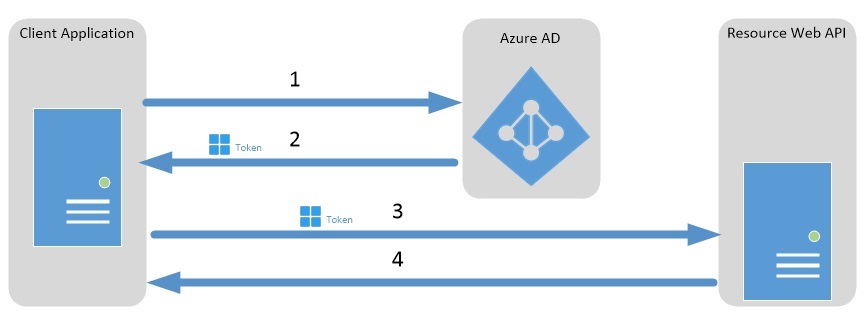
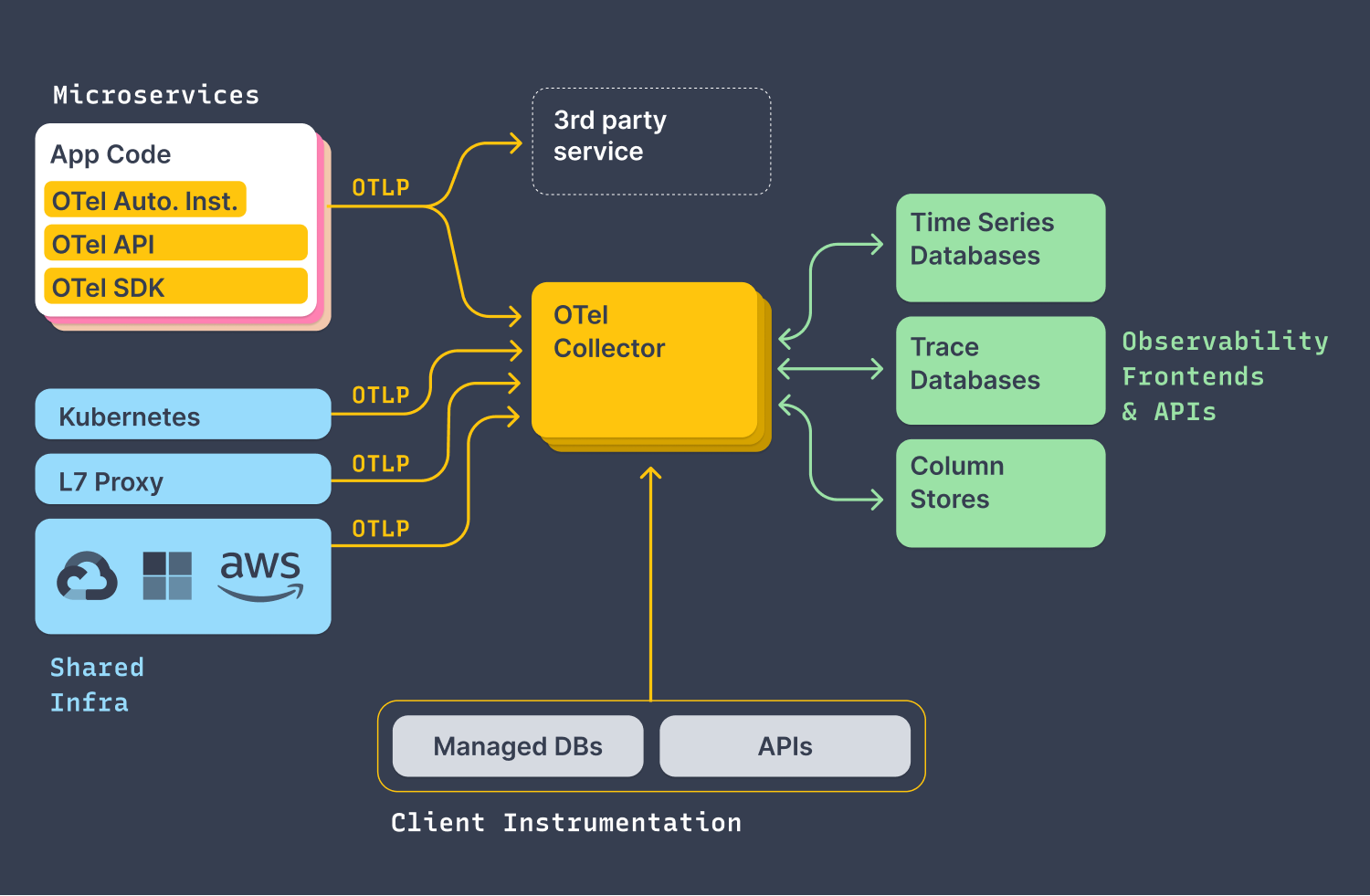
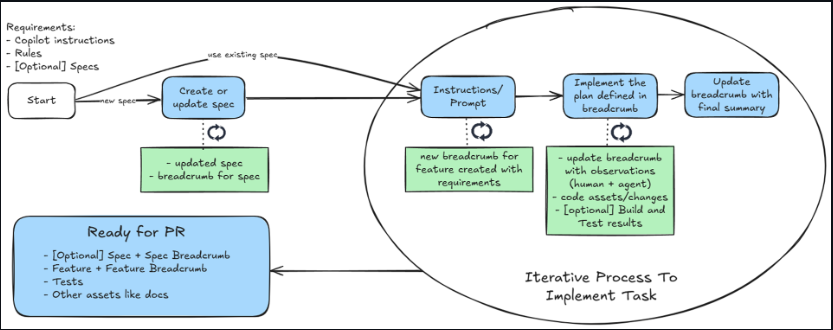
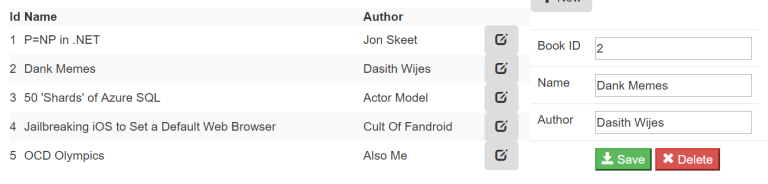
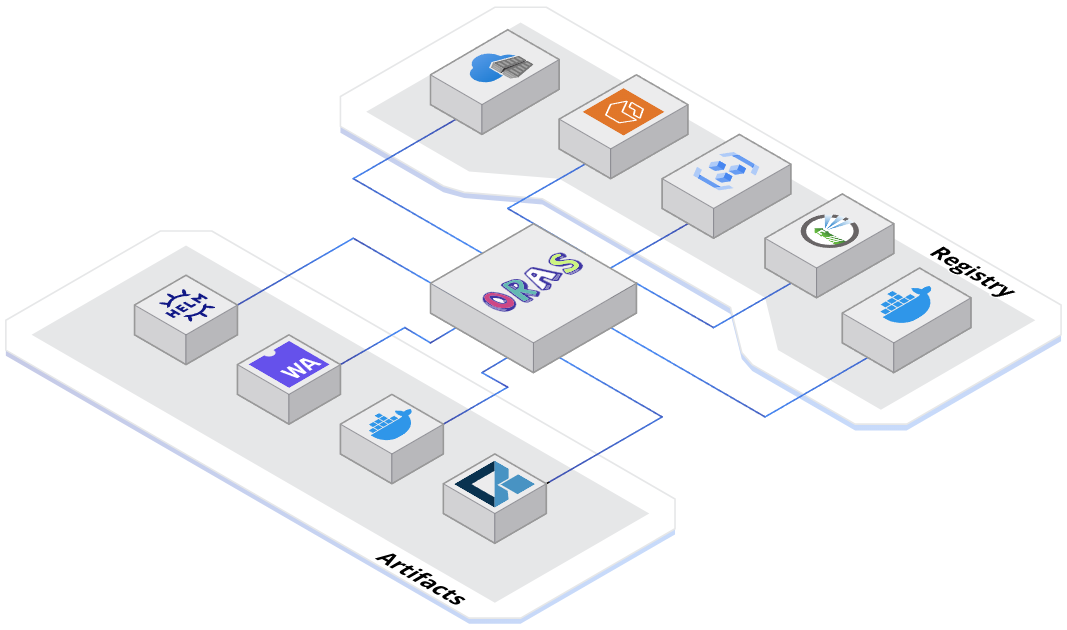
Lessons from the Trenches in a LLM Frontier: An Engineer’s Perspective - Apidays Australia 2024
I, along with my colleagues Jason Goodsell and Juan Burckhardt, had the opportunity to present our key insights and learnings from the rapidly evolving world of Large Language Models (LLMs) at Apidays Australia 2024 in October. The talk, titled “Lessons from the Trenches in a LLM Frontier: An Engineer’s Perspective,” shared our experiences from the front lines of developing LLM-powered solutions. Our team has been deeply immersed in creating and integrating LLM solutions, observing firsthand the industr...